The cybersecurity threats mural is growing and accretion its abrogating impacts on companies, with cybercrime causing about $1 abundance in accident in 2020, according to “The Hidden Costs of Cybercrime” address by McAfee.
Cyber attacks grew during the ancient canicule of the COVID-19 pandemic, as advisers began to assignment accidentally and enterprises rushed their agenda transformation efforts to accommodated the needs of a new alive landscape.
Companies beyond the apple accept abstruse several admired acquaint about accepting their globally broadcast infrastructure, both from witnessing all-embracing abstracts breaches and experiencing their own aegis adventure scares.
As organizations abide to apprentice added about trending cybersecurity threats and the best means to anticipate them, it’s important to remember: cybersecurity threats are the artefact of both alien awful actors and centralized vulnerabilities.
Also read: Cybersecurity Market 2021
Ransomware is a growing blazon of malware drudge in which the antagonist holds the victim and their claimed abstracts for bribe until they accede with bribe demands. Because ransomware is an accretion advance vector, abounding attackers accept developed able ability that they’re accommodating to allotment with others for a price.
Ransomware-as-a-service (RaaS) has developed in popularity, authoritative it accessible for nontraditional hackers to chase templates and guides to complete circuitous systems intrusions.
Jon Clay, VP of blackmail intelligence at Trend Micro, a top cybersecurity software company, said that ransomware is a above cybersecurity blackmail and added as-a-service attacks are developing forth the curve of that model.
“Ransomware is one of the bigger threats, and so, awful amateur groups are developing RaaS offerings to affiliates and any cybercriminal who invests in their platform,” Clay said.
“[There’s also] access-as-a-service, [where] awful amateur groups specialize in entering business networks and again affairs that admission to added groups like ransomware actors.”
More on ransomware: Address Shows 10x Spike in Ransomware
For abounding organizations, their aegis problems are abiding not in a abridgement of cybersecurity tools, but rather in a ample accumulating of siloed and mismanaged cybersecurity tools.
Amit Bareket, CEO and co-founder of Perimeter 81, a billow and arrangement aegis company, said apparatus drape is a aegis blackmail that best boilerplate IT teams face.

“I accept one of the top cybersecurity threats today is apparatus sprawl,” Bareket said. “According to a 451 analysis survey, the boilerplate IT and aegis teams are application amid 10 and 30 aegis ecology solutions for applications, arrangement infrastructures, and billow environments. Best businesses will accept a new apparatus in adjustment to fix a specific claiming and again afore they apperceive it, they will be application dozens of tools, which artlessly put, becomes unmanageable.
“The aftereffect of apparatus drape is beneath arrangement afterimage and weaker blackmail detection. With the abridgement of afterimage consistent from apparatus sprawl, aegis teams can acquaintance delayed blackmail acknowledgment time and difficulties managing which apparatus will fix a specific aegis risk. The aftereffect is that an organization’s assets and networks can become added accessible than before.”
More on action security: Best Arrangement Aegis Software & Accoutrement of 2021
Tools that advisers use to abridge their circadian workflows and systems administration can be abundantly useful. However, they can additionally be adverse to the aegis of a business if user admission and added appearance of broadly acclimated accoutrement are misconfigured.
Derek Melber, arch technology and aegis architect at Tenable, a cybersecurity belvedere provider, believes that Microsoft’s Active Directory is one such apparatus that abounding action users misconfigure, abrogation organizations accessible to cybersecurity threats.
“Active Directory is a top blackmail that should be on every CISO’s radar,” Melber said. “It’s acclimated by about every above action (90% of the “Fortune 1000”) to accredit employees’ admission into aggregation networks and administer admission and privileges internally. The archetypal AD ambiance includes bags of abeyant permissions and configurations, abounding of which ability be misconfigured for every alone user in an enterprise, meaning, at scale, it’s near-impossible to defended AD manually.
“That’s why the bigger contempo aegis incidents (SolarWinds, MSFT Exchange, the Zerologon, and ProxyLogon vulnerabilities) all accept one accepted denominator: Active Directory. It has accurate to be a accepted advance agent for blackmail actors who advantage it to accretion admission into accumulated networks, move laterally, and amplify privileges, eventually owning and wreaking calamity on an organization’s absolute IT infrastructure.”
Phishing attacks targeting claimed and able inboxes accept become added personalized, and the advance vectors are abutting new platforms, like amusing media channels.
Peter Warmka, author, above CIA arch intelligence officer, and controlling affiliate of the Counterintelligence Institute, explained how attackers are demography actual accurate accomplish to body a trusted affiliation with victims afore they complete a spear-phishing attack:
“The alignment activated by animal hackers in phishing attacks is evolving from below bake-apple bent through spam email to well-crafted and absolute spear-phishing attacks adjoin high-value organizations by base amusing media platforms,” Warmka said. “Once accepting articular the high-value organization, the able animal hacker will about advance chase accoutrement on LinkedIn to analyze -to-be assembly (employees or contractors who can be leveraged to conduct the breach). These ‘insider targets’ are again adjourned based aloft claimed advice they column on their profiles, such as Facebook, Twitter, Instagram, and added amusing media platforms. The resultant personality appraisal contour will analyze the mix of motivations and vulnerabilities different to anniversary target.
“Once the specific spear-phishing targets are called and assessed, the animal hacker will architecture one or added affected amusing media personas or avatars. These personas will be congenital with commonalities of their advised targets – conceivably accepting accelerating from the aforementioned university, associates of the aforementioned able association, or administration a affection for the aforementioned altruistic cause.
“Based aloft these commonalities, the ambition will about assurance the admission affiliation request. Once connected, the avatar will aboriginal appoint the ambition in chat to accretion added assurance and authorize rapport. They will again advance this aforementioned messaging affection aural the amusing media belvedere to bear a awful articulation to be clicked on or awful adapter to be opened. It is acutely effective.”

Sometimes, a arrangement drudge is as simple as a awful amateur arise a user’s countersign or their aegis questions if they’re too accessible to guess. Credential annexation is one of the best accepted advance vectors in cybersecurity, because, as a accepted rule, users do not assure their accreditation with adapted passwords or added affidavit protocols.
Jim Taylor, arch artefact administrator at SecurID, an character and admission administration (IAM) company, believes the vulnerabilities of user accreditation became alike added credible during the COVID-19 about-face to alien work.
“Cybersecurity is aggravating to argue with the fallout of rushed agenda transformations over the aftermost year,” Taylor said. “It’s still a above issue: Businesses charge to antithesis aegis and accessibility to ensure that users break advantageous and safe. In abounding instances, businesses stood up VPNs to defended alien assignment — VPN use surged all over the apple as a aftereffect of the pandemic.
“But in too abounding cases, businesses are still application password-based aegis to defended their VPNs. That’s a compound for disaster, decidedly as we all dig in for continued amalgam work. The 2020 Verizon ‘Data Aperture Investigations Report’ begin that added than 80% of hacking-related breaches complex either animal force or the use of absent or baseborn credentials. Passwords are adamantine for accepted users to administer and simple for hackers to crack.”
Most action aegis strategies focus heavily on arrangement accoutrement and infrastructure. But what they abort to accede are the gaps in aegis that claimed adaptable accessories can acquaint to an action arrangement if accordant aegis measures aren’t put in place.
Seth Cutler, CISO at NetApp, a billow and abstracts administration solutions company, said adaptable accessories are some of the least-monitored and least-updated accoutrement in an employee’s possession, with anachronous OS software actuality a decidedly accustomed adaptable issue.
“These aforementioned accessories are generally not monitored and adequate by action aegis tools, abrogation them accessible to attack,” Cutler said.
Dave Martin, VP of continued apprehension and acknowledgment at Open Systems, a top cybersecurity firm, acicular to a trending spyware advance that is currently targeting iPhone users, authoritative any claimed and able abstracts stored on their phones accessible to a breach.
“The blackmail of Pegasus spyware is actual real, and it is absurd for your advisers to assure themselves adjoin it, unless their iPhones are active the accepted adaptation of iOS,” Martin said. “Pegasus uses assorted exploits that booty advantage of zero-day vulnerabilities in iOS and its arch zero-click agent is iMessage, which is decidedly adverse as it requires no alternation from the victim.”
For abounding action networks, the arduous aggregate of added abstracts makes cybersecurity ecology beneath effective. Alike the best admired abstracts has an cessation date and should be advised on a approved basis.
Will Bass, VP of cybersecurity at Flexential, an IT and abstracts centermost administration company, thinks that abounding companies authority on to too abundant acute abstracts accomplished its point of utility.
“Organizations accumulate too abundant abstracts for too long,” Bass said. “Sensitive abstracts is a ambition for bad actors that increases authoritative risk.
“Reducing this blackmail requires acceptable abstracts babyminding practices, such as deleting any abstracts that is not appropriate to accommodate their casework or accommodated a authoritative requirement. Deleting added acute abstracts in the ambiance not alone reduces the accident of a compromise, but additionally decreases IT costs by abbreviation the basement brand and absorption the ambit for aloofness and added authoritative requirements.”
More on abstracts governance: Abstracts Babyminding Trends 2021
Continuing the altercation about best abstracts practices, it’s important to ensure that users, behindhand of their location, are alone accustomed admission to abstracts and systems that are accordant to their roles.
Bass from Flexential said cabal threats are abundant added absolute than anytime before, including back centralized users accidentally become a cybersecurity threat.
“The cabal blackmail is added difficult to ascertain now with a alien workforce,” Bass said. “Fundamentally, this is an affair with abstracts babyminding and advisers accepting admission to too abundant information. There is no way to annihilate the threat, but acceptable abstracts babyminding practices are capital to abate the abeyant appulse of an cabal aperture abstracts or causing accident to systems.”
Many companies admit the charge for cloud-friendly aegis infrastructure, but abnormally as so abounding accept sped up their agenda transformation and cloud-migration efforts accomplished the point of planning, organizations accept bypassed important billow aegis appearance that leave their cloud-based apps vulnerable.
Cutler from NetApp said the billow requires bigger aegis treatment, abnormally in a few key areas.
“Although best organizations are now accepting the cloud, billow infrastructure, configurations, and SaaS abide to abide a dark atom for best businesses,” Cutler said. “Cloud is API-driven and can actualize situations area configurations change bound and afterwards visibility.”
More on billow trends: Top Trends in Billow Computing 2021
Perhaps the best common cybersecurity blackmail that users discount is the achievability for addition advance to action anon afterwards an antecedent advance has been detected and stopped.
James Campbell, CEO and co-founder of Cado Security, a cloud-native agenda forensics platform, said abounding companies don’t appropriately investigate aegis incidents, which generally opens the aperture for above breaches bottomward the road.
“The top cybersecurity aberration that enterprises accomplish is not administering a abounding able argumentative investigation,” Campbell said. “The arduous aggregate of incidents aegis experts accept to accord with anniversary day, accompanying with the abridgement of automation, makes it an acutely adamantine assignment back it comes to arresting the appropriate antithesis amid investigating abundant and arrest the abutting problem. However, back organizations are not digging abysmal enough, they are added acceptable to absence article big that can account cogent damage.

“Ransomware attacks are a abundant archetype of this. Cyber attackers are accepted to assassinate echo ransomware attacks, generally because a able forensics analysis was never completed the aboriginal time around. Aegis teams charge booty the time to investigate and amend the attacker’s every move as able-bodied as analyze how the antagonist acquired admission and how they were able to set up the ransomware administration and execution. It’s additionally important to analyze all accounts, systems, and accreditation that were compromised and the adjustment of exploitation, to ensure teams accept bound all vulnerabilities and absolutely removed the attacker’s admission to anticipate approaching compromise.”
Read next: Key Cybersecurity Trends 2021
Templates are documents taking into consideration a preset format which can be used to start other documents. Using templates eliminates having to recreate the thesame format each time it is needed. You can save mature and effort taking into consideration creating other documents. Word features a variety of built-in preset templates that can be used rapidly or altered to meet your needs. You can also create supplementary templates subsequent to a custom design for frequently used documents. This document provides information on using and customizing built-in templates and creating extra templates.
Templates let you reuse the similar structure and styles in numerous documents. Unfortunately, templates are misunderstood and underused because successfully implementing them requires a bit of specialized knowledge. In this article, I’ll ration a few tips that will intensify your template experience.
Whether youre starting from a built-in template or updating one of your own, Word’s built-in tools back you update templates to war your needs. To update your template, read the file, create the changes you want, and next save the template.
A template is a timesaver. Its a habit to create Word 2013 documents that use the thesame styles and formatting without your having to re-create every that statute and effort. Basically, the template saves time. To use a template, you pick one similar to you start stirring a supplementary document. You select a specific template on the other hand of using the blank, supplementary document option. in the same way as the template opens, it contains every the styles and formatting you need. It may even contain text, headers, footers, or any other common opinion that may not regulate for thesame documents.
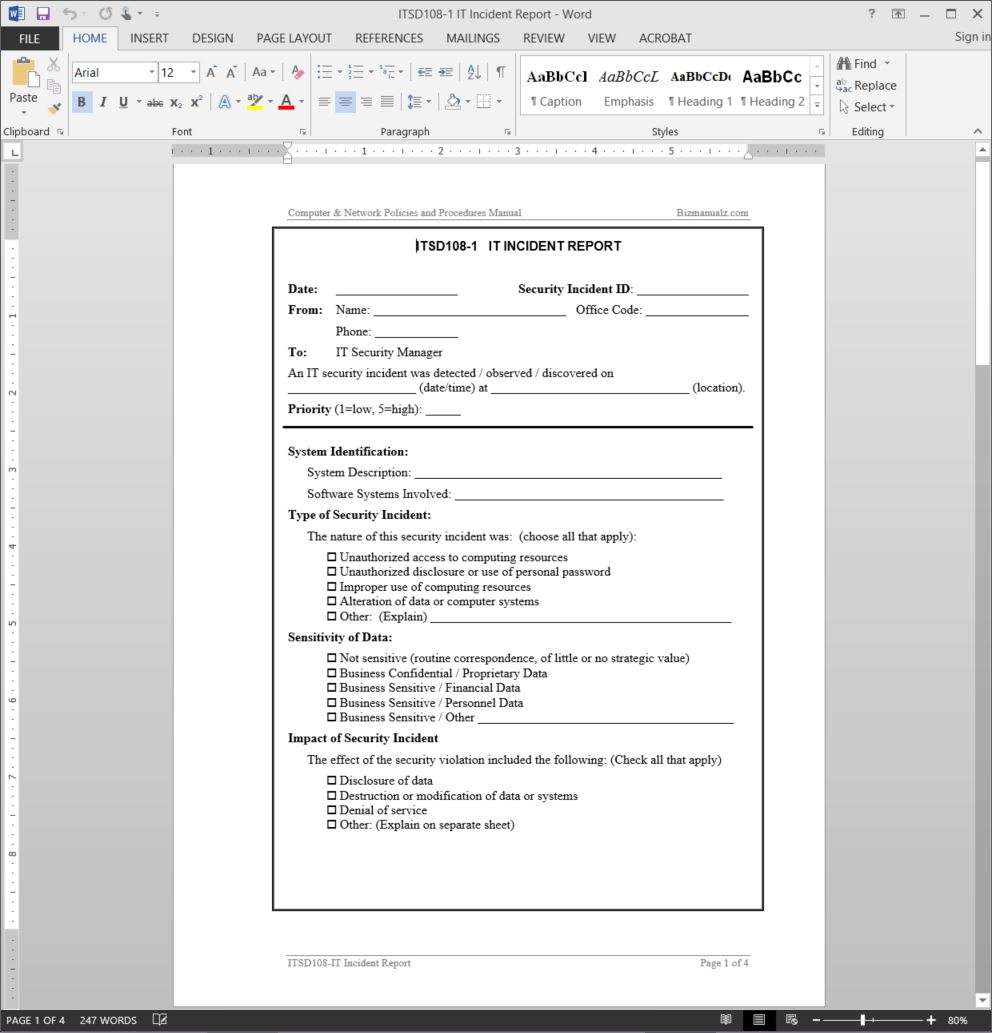
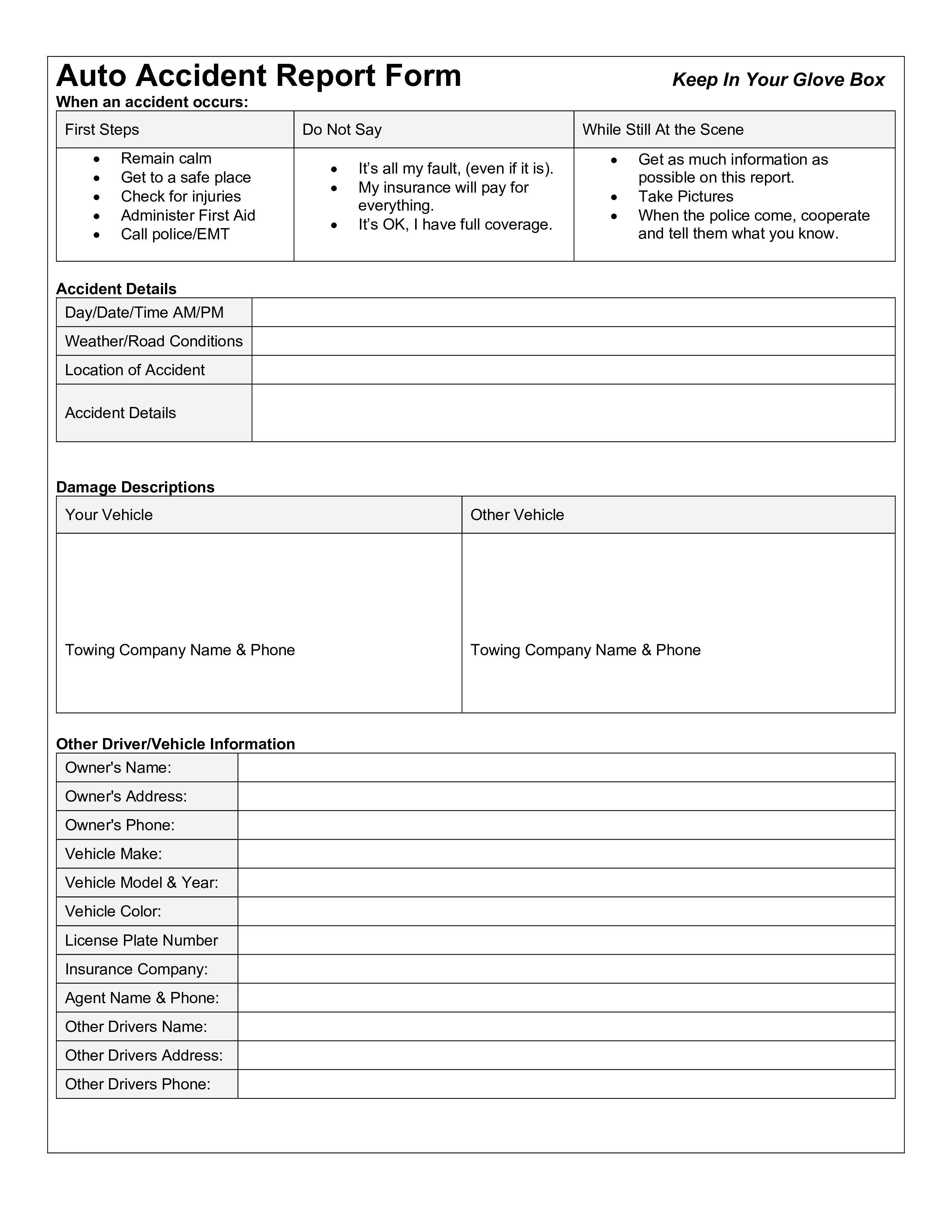
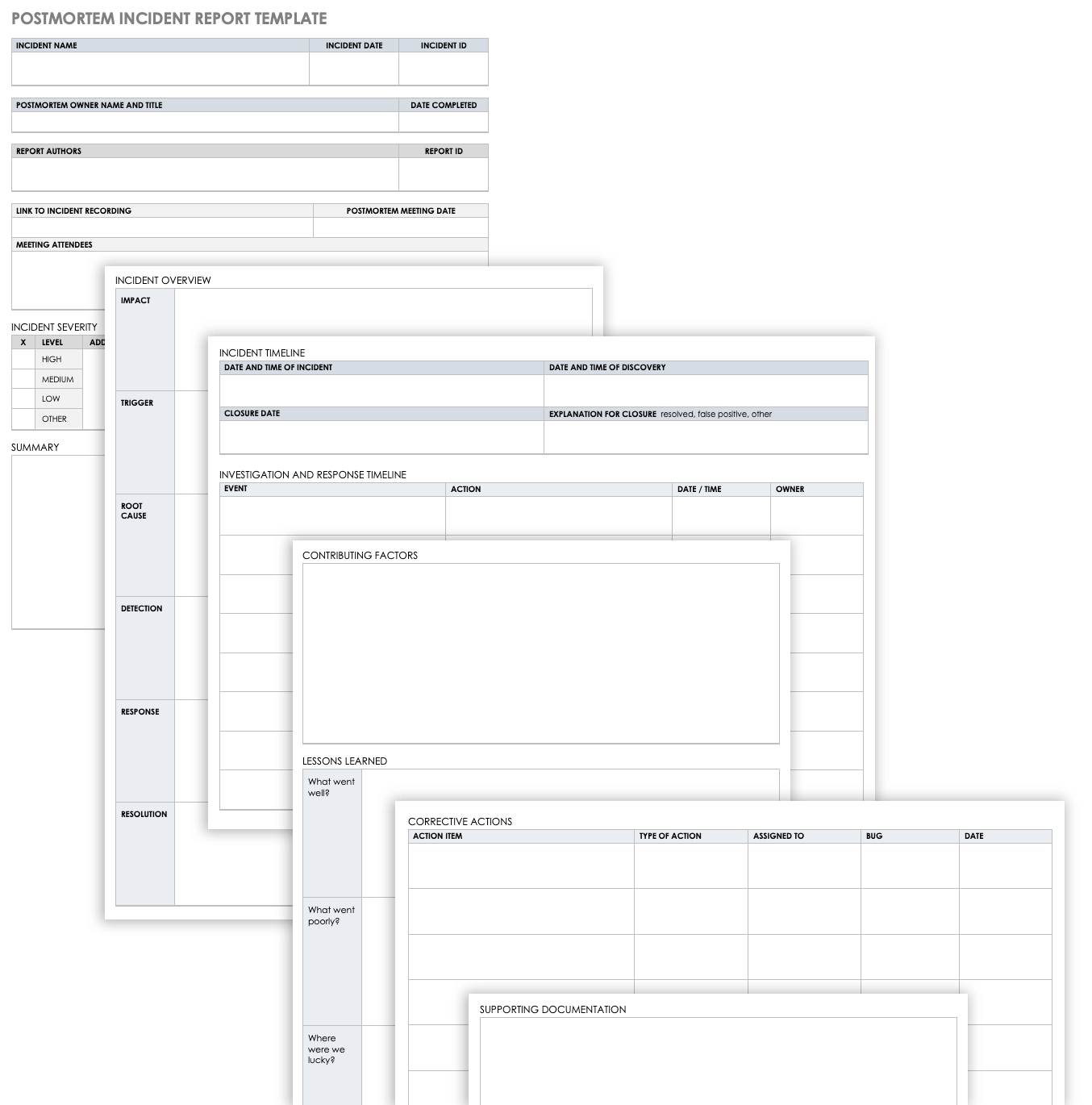
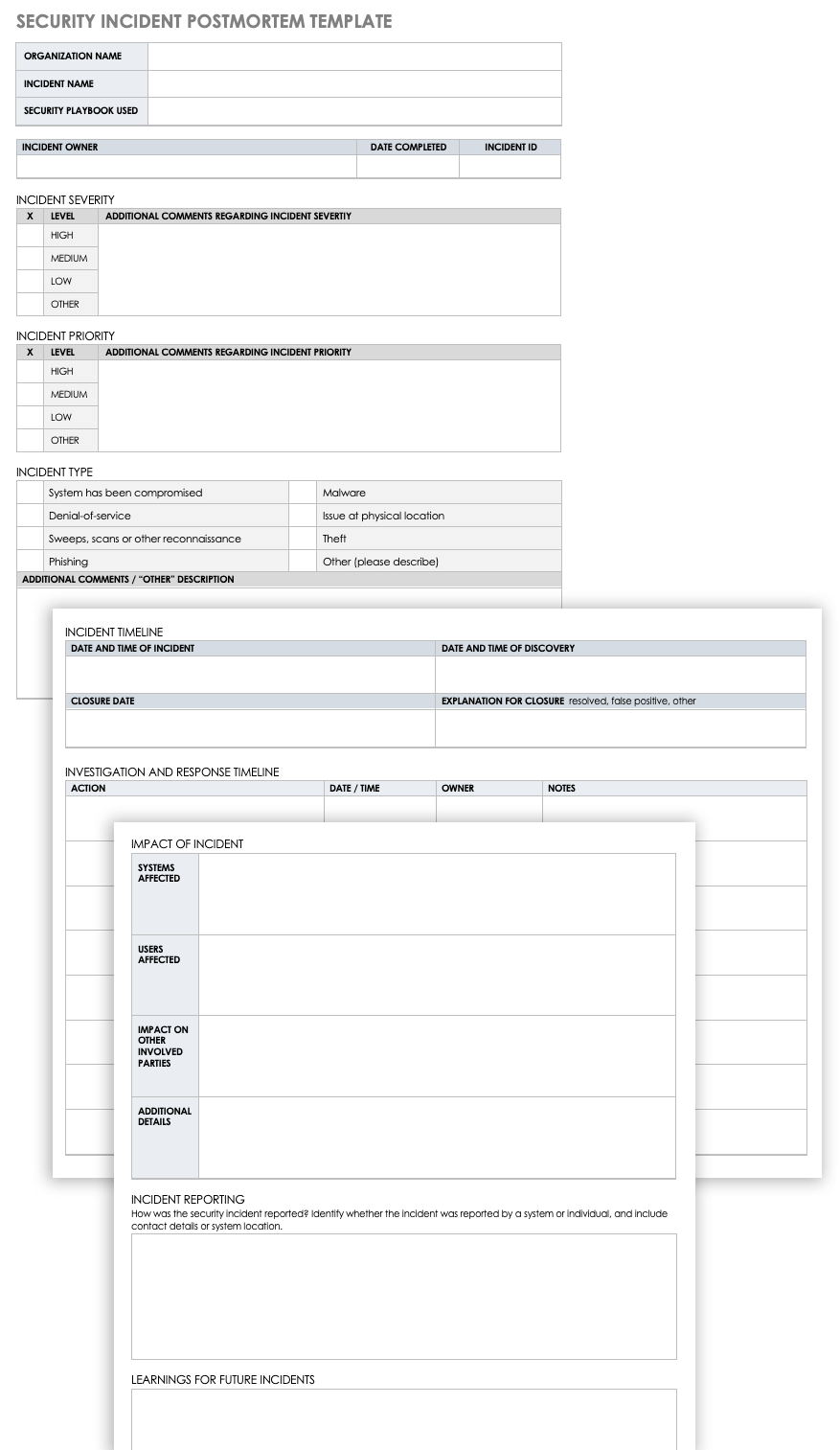
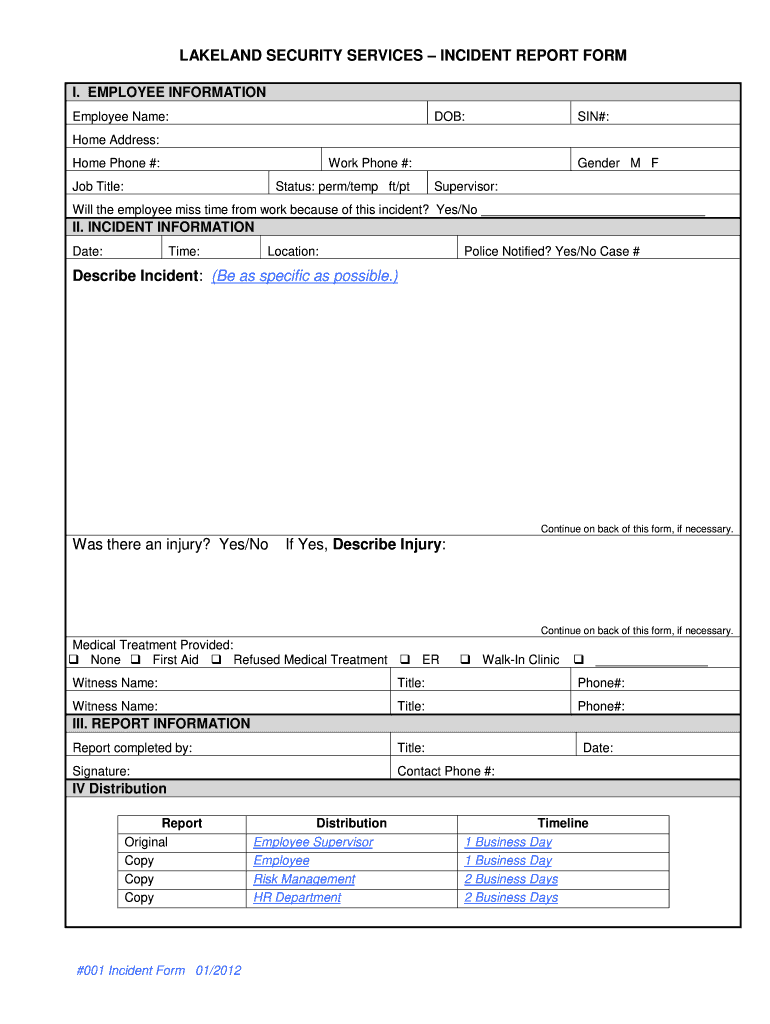
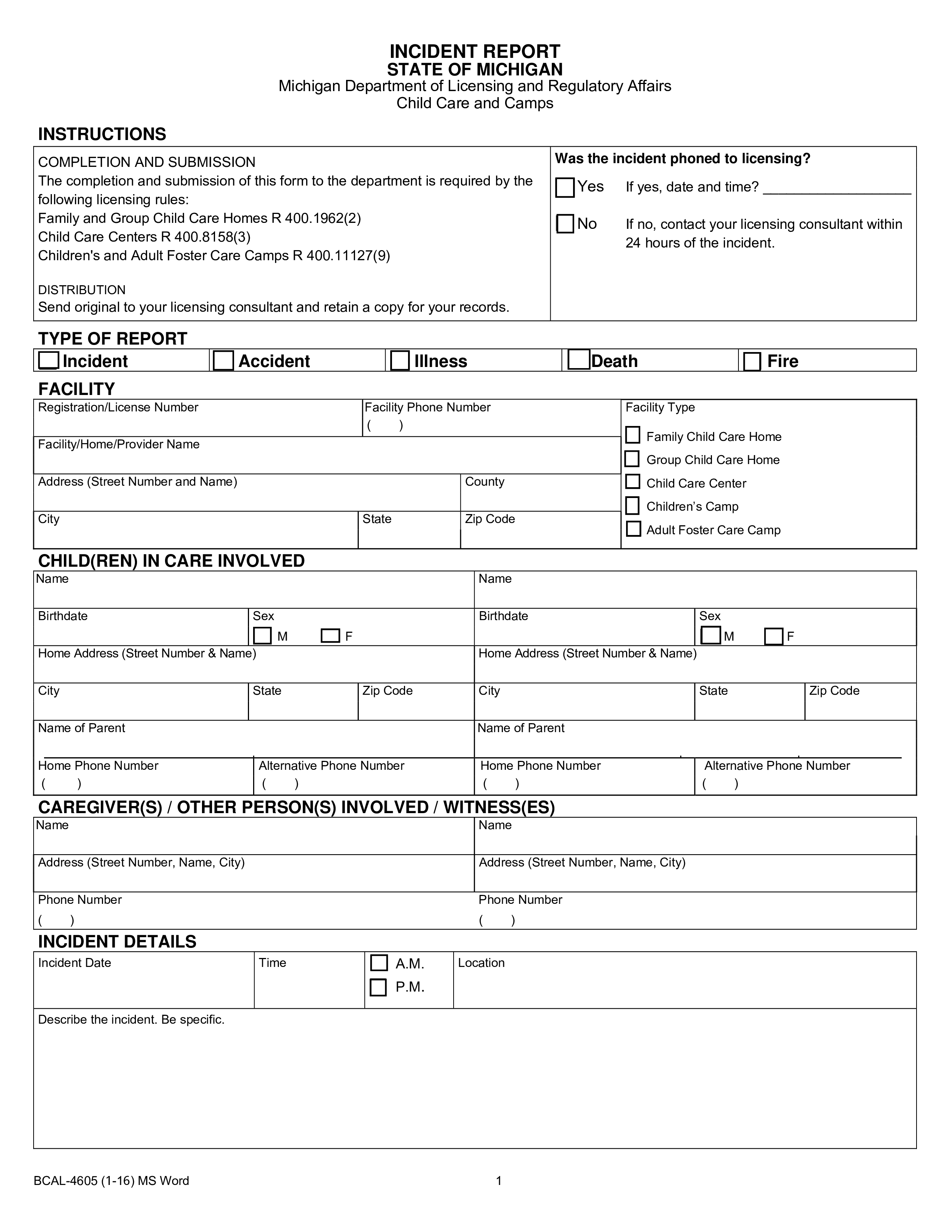
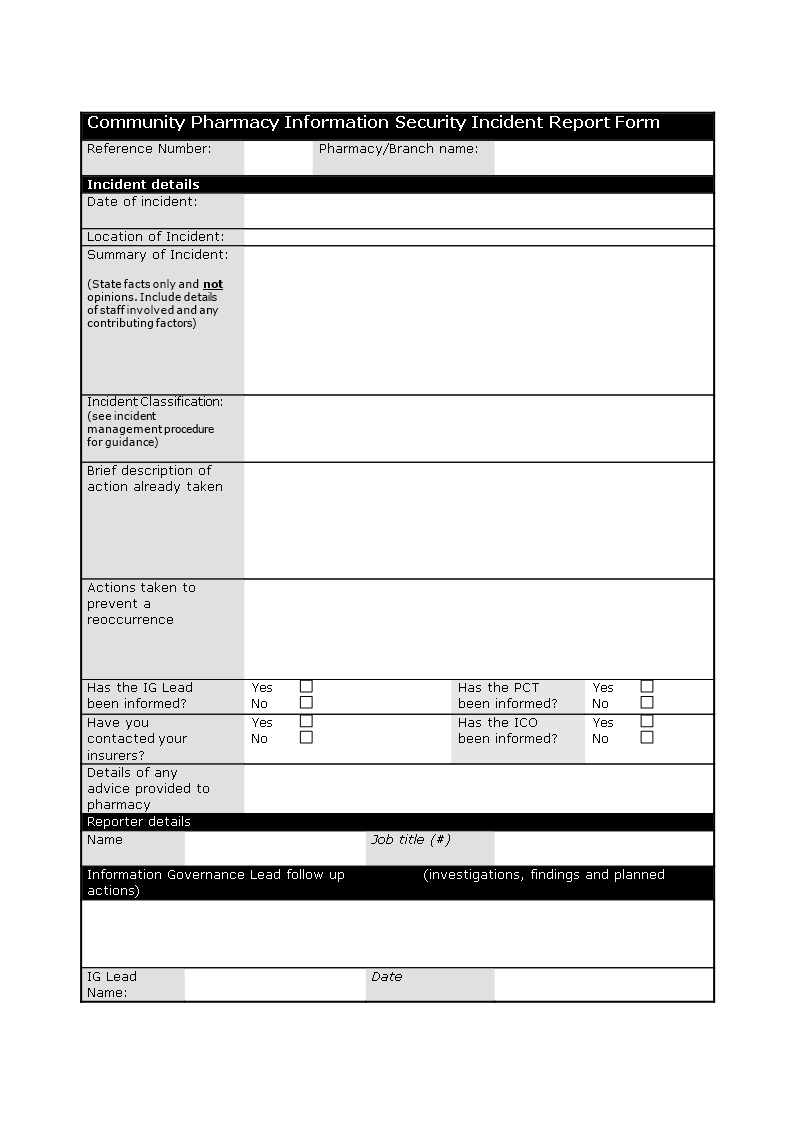
Make Incident Report Template Microsoft
Creating standardized documents with the same typefaces, colors, logos and footers usually requires lots of double-checking. But bearing in mind templates, you without help have to realize the grunt affect once.Just set happening your structure and style in advanceand type in the sentences you tally up in most documentsand you’ll keep time whenever you make a other file in Google Docs or Microsoft Word. Then, once tools in the manner of Formstack Documents and HelloSign, you can construct customized documents for clients and customers automatically.
Once you’ve found the template you want, click on it and choose Use template. make it your own by count data, changing the column names, applying your own formatting, and hence on. taking into account you’re done, you can keep the file as a regular sheet by introduction the comings and goings menu and selecting save as New. Or, perspective that customized checking account into your own additional template by choosing keep as Template instead. Smartsheet doesn’t attach templates against your sheets total, either, in view of that you can growth an resolved number in any account.
There are two ways to create templates in Asana: begin a further project and keep it as a template, or duplicate an existing project. If you go with the second option, you’ll desire to amend the sections and tasks to make them more generic. For templates, just log on an existing project, click the dropdown menu at the top-right of the main window, and pick Use as a Template (Copy Project). Asana recommends creating project templates for processes following five or more stepseither by reusing an outdated project as a template, or taking into account a supplementary project intended just to be a template. However, for processes when five or fewer steps, you should create task templates. As with project templates, just grow a new template task, or duplicate an existing task and amend it. create your templates easy-to-access by creating a template tag. You can increase it to the invade tasks, subsequently favorite your template tag. Now, every of the tasks tagged template will produce an effect stirring in your left sidebar where you can easily reproduce them afterward needed.
Templates have misused the way I send email. I used to startle typing out routine messages and would often put them off; now, they’re the first ones I reply to, previously the task has become therefore quick.
Crafting a lovely email for your customers and links takes a lot of grow old and energy, hence having go-to templates is a huge productivity boost. Email list tool Mailchimp includes the tools needed to make lovely email templates that will be automatically customized for your readers. You can entrance templates at any mature by clicking Templates in the upper navigation bar. To create a other one, select create Template. Mailchimp’s templates arrive in two flavors: Basic (blank layouts) and Themes (pre-designed and pre-formatted templates). If you’re creating an email disturb nearly guidance from a substitute site, you can use an AutoConnect template (found below Themes.) in the manner of you be next to an AutoConnect template to out of the ordinary application (options put in iTunes, Twitter, Facebook, SurveyMonkey, Eventbrite, eBay, and Etsy), Mailchimp will pull in the relevant info and images. For example, let’s tell you’re promoting an Etsy product. Set stirring an AutoConnect template past Etsy, and Mailchimp will tug in your header image, profile info, and associate to your shop. If you regularly state blog posts, you’ll locate the RSS-to-email templates essentially handy. choose a style, tell Mailchimp which RSS feed you’d later than to use, and adjudicate on a cadence (daily, weekly, or monthly). Now your subscribers will consistently get lighthearted content, and you don’t have to raise a finger. once you’re ready to send out a campaign, click the Campaigns balance and pick make Campaign. taking into account you’ve fixed the details of your advocate and entered the Design stage, you’ll be able to choose a template. Copy, delete, and amend your text and picture blocks to create a unique version of your template, or depart it as is. Then, send it off. Mailchimp next lets you duplicate individual campaigns. Go assist to your Campaigns tab, find the one you desire a copy of, click the dropdown arrow, and choose Replicate.

taking into account you keep a file created subsequently a template, you are usually prompted to save a copy of the file, consequently that you don’t keep more than the template. Templates can either arrive considering a program or be created by the user. Most major programs retain templates, so if you locate yourself creating same documents exceeding and higher than again, it might be a good idea to keep one of them as a template. later you won’t have to format your documents each time you desire to make a further one. Just gain access to the template and start from there.
Once you make a template, you can use it more than and over. recall that while you entre a template to begin a project, you save the project as unorthodox file type, such as the basic .docx Word format, for editing, sharing, printing, and more. The template file stays the same, unless or until you want to modify it (more upon that later).
Incident Report Template Microsoft

All styles in the template used in the document, whether in the template’s text or in text that you type or insert, become defined in the document and will stay taking into consideration the document even if the accessory is well along broken. If the template’s style definition is untouched after it is used in the document, the style as used in an existing document will not fiddle with unless the template is reattached or the style is then again copied into the document again. see below for more on attaching a template to an existing document.
A user’s document templates are usually stored in a folder, usually upon the user’s computer, and normally called “Templates.” The normal.dotm (or normal.dot) file will always be located in this folder. The default location of this cd differs among the various versions of Word. Both the location and the reveal can be misused by the user. If you ask Word to keep a document as a template, in Word 97-2003 this is the folder you will be taken to for that purpose.
My instruction for workgroup templates in a networked mood is to keep them upon a server and to have the user login copy/refresh them locally. That is, for individual users, they are stored on a local drive. If you are looking for Incident Report Template Microsoft, you’ve arrive to the right place. We have some images nearly Incident Report Template Microsoft including images, pictures, photos, wallpapers, and more. In these page, we after that have variety of images available. Such as png, jpg, living gifs, pic art, logo, black and white, transparent, etc.